System Linux has two types of users:
Privileged:
- root – used for managing the system with no restrictions
- system users – required to run services, i.e. MySQL Admin account
Unprivileged:
- regular (standard) users
User creation process
Creating users on a Linux system may initially seem complex, but it follows a logical process. A few config files play a crucial role during this process. The diagram below illustrates what happens when a system administrator executes the “useradd” command.
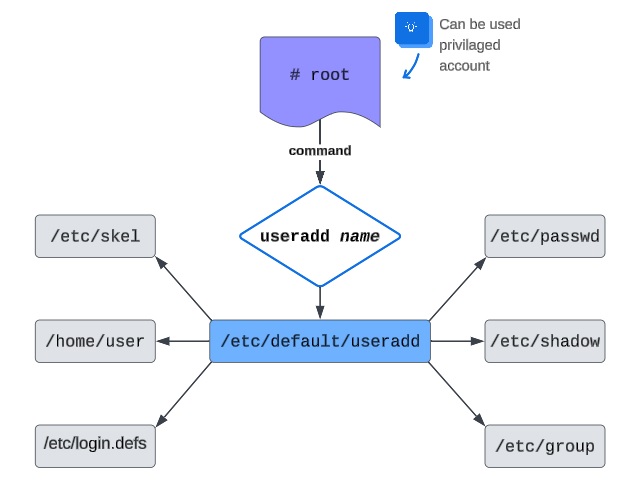
Let’s take a closer look at each section.
/etc/default/useradd
[root@RedHat ~]# vim /etc/default/useradd # useradd defaults file GROUP=100 HOME=/home INACTIVE=-1 EXPIRE= SHELL=/bin/bash SKEL=/etc/skel UID_MIN=1000 UID_MAX=5000 GID_MIN=1000 GID_MAX=3000
Key fields of the file:
- GROUP=100 [default value 100 means that the group name will be the same as the user name]
- HOME=/home [default home directory]
- INACTIVE=-1 [inactive days after password expires, and account locked, “-1” never expires]
- EXPIRE=None [default expiration date for new accounts]
- SHELL=/bin/bash [default shell for new accounts]
- SKEL=/etc/skel [path to default skeleton directory containing default configuration]
- UID_MIN=1000 and UID_MAX=5000 [range of user IDs for new accounts]
- GID_MIN=1000 and GID_MAX=3000 [range of group IDs for new groups]
/etc/passwd
[root@RedHat ~]# vim /etc/passwd peter:x:1000:1000:peter:/home/peter:/bin/bash apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
As we can see in the example, the account record is divided into seven sections, each separated by a colon.
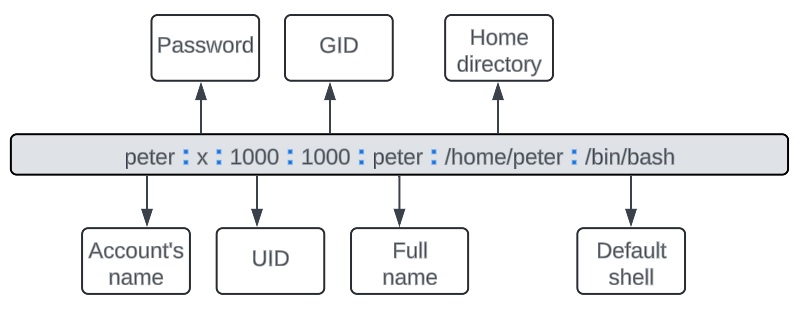
It is important to emphasize that passwords are saved in a shadow file.
/etc/shadow
This file contains information about each account’s password. In the snippet example below, each record represents an individual account.
[root@RedHat ~]# vim /etc/shadow root:$6$Q7P-encrypted-password-V6xA9Q::0:99999:7::: peter:$6$Q7P-encrypted-password-V6xA9Q:19896:30:90:3::: apache:!!:19931::::::
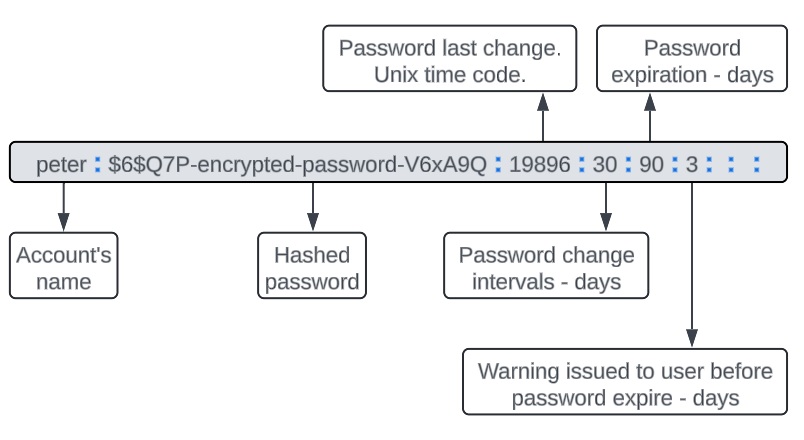
/etc/login.defs
The /etc/login.defs file in Linux is a configuration file that sets the system-wide defaults for user account creation, password policies, and other login-related settings. Adjusting these settings, system administrators can enforce security policies and customize the behaviour of user accounts. Let’s take a closer look at the snippet example below.
[root@RedHat ~]# vim /etc/login.defs UMASK 022 PASS_MAX_DAYS 99999 PASS_MIN_DAYS 0 PASS_WARN_AGE 7 PASS_MIN_LEN 8 # Min/max values for automatic uid selection in useradd(8) # UID_MIN 1000 UID_MAX 60000 # Max number of login(1) retries if password is bad # LOGIN_RETRIES 3 # # Max time in seconds for login(1) # #LOGIN_TIMEOUT 60 # This option is overridden with the -M or -m flags on the useradd(8) # command-line. # ENCRYPT_METHOD SHA512 SHADOW yes CREATE_HOME yes
Key fields of the file:
- UMASK – determining file permission defaults for new files and directories
- PASS_MAX_DAYS – maximum number of days a password remains valid before it must be changed
- PASS_MIN_DAYS – minimum number of days required between password changes to prevent users from changing their passwords multiple times in quick succession
- PASS_WARN_AGE – number of days before password expiration that users are warned
- PASS_MIN_LEN – minimum length for new passwords
- LOGIN_RETRIES – number of allowed login attempts before locking the account
- LOGIN_TIMEOUT – time in seconds before a login session times out if no input is received
- ENCRYPT_METHOD – the method used to hash account passwords
- SHADOW – shadow passwords
- CREATE_HOME – create a home directory by default
Group creation process
Every single user can belong to multiple groups (minimum one). The user’s primary group is defined in /etc/passwd
Administrators can control access to files, directories, and system resources by assigning users to groups. The group configuration files can be modified using vigr. This command opens the editor on the /etc/group
[root@RedHat peter]# vigr peter:x:1000: ross:x:1001: monica:x:1002: rachel:x:1004: phoebe:x:1005: joey:x:1006: chandler:x:1007: actor:x:1008:monica,chandler,ross,joey,phoebe,rachel director:x:1009:ross screenwriter:x:1010:monica,ross,rachel apache:x:48: newtest:x:1011: latestgroup:x:1055: wireshark:x:975: usbmon:x:974:
Let’s take a closer look at one of the records.
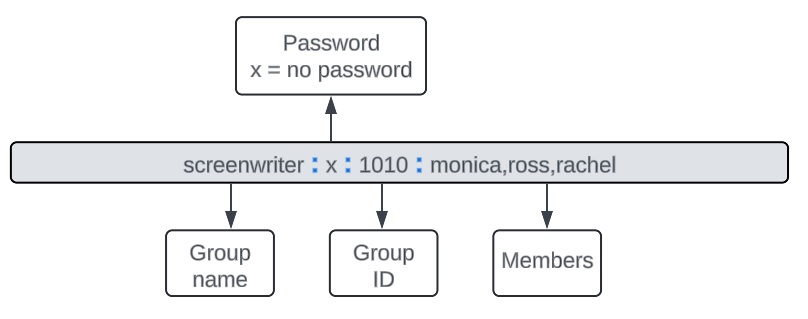
If we would like to check who is a member of a specific group, we can execute the List Identity command lid -g screenwriter, as shown in the example below:
[root@RedHat peter]# lid -g screenwriter monica(uid=1002) ross(uid=1001) rachel(uid=1003) [root@RedHat peter]#
Creating a new group is a straightforward process; use groupadd followed by the group’s name.
Most common management commands
- useradd new_user_name -> creating a new user
- passwd user_name -> create a password for user
- groupadd name_of_the_new_group -> creating a new group
- usermod -aG director monica -> adding a user “monica” to the “director” group
- id rachel -> showing all memberships for a particular user. Example below:
[root@RedHat ~]# id rachel uid=1003(rachel) gid=1004(rachel) groups=1004(rachel),1008(actor),1010(screenwriter)
- chage -l user_name -> check password management settings. Example below:
[root@RedHat ~]# chage -l rachel Last password change : Jun 22, 2024 Password expires : Sep 20, 2024 Password inactive : never Account expires : never Minimum number of days between password change : 30 Maximum number of days between password change : 90 Number of days of warning before password expires : 3
- userdel user_name -> remove a user
- userdel -r user_name -> remove a user and the complete user environment